Sheding Light into the HFT Dark Forest
DeFi High-Frequency Trading
Programmable Money enables promicious actors to extract financial value from intertwined smart contracts. We have quantified how much in our ground-breaking IEEE Security & Privacy paper.
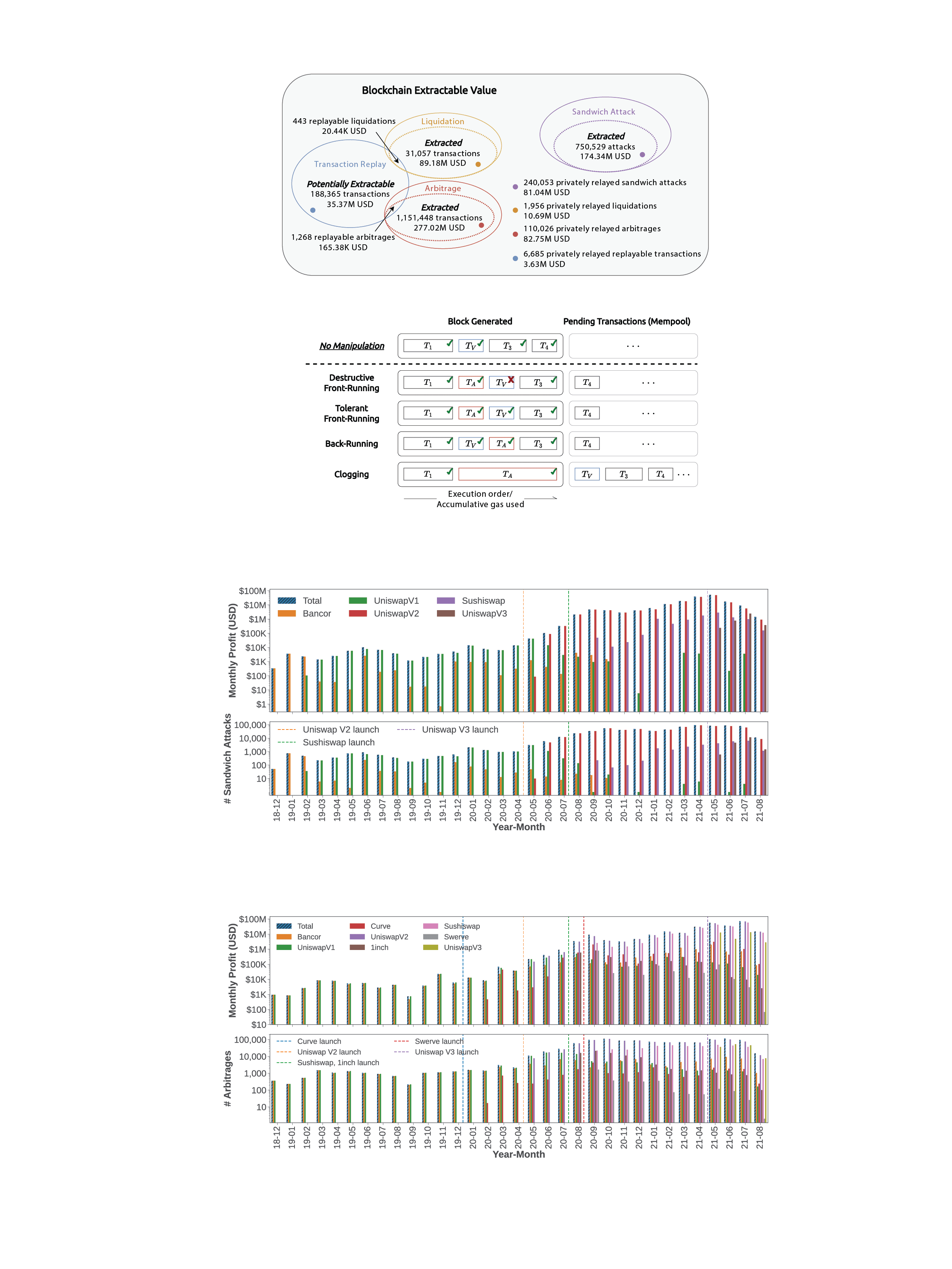
We overview of various sources of blockchain extractable value and find that sandwich attacks, liquidations and arbitrage yield 540.54M USD of BEV over 32 months. We evaluate a novel application-agnostic transaction replay algorithm, which could have extended BEV by 35.18M USD.
- Comprehensive BEV Quantification We are the first to comprehensively measure the breadth of BEV from known trading activities (i.e., sandwich attacks, liquidations, and arbitrages).
- Naive Imitation Transactions We are the first to propose and empirically evaluate a transaction replay algorithm, which could have resulted in 35.37M USD of BEV. Our algorithm extends the total captured BEV by 35.18M USD, while intersecting with only 1.43% of the liquidation and 0.11% of the arbitrage transactions.
- P2P Overhead vs. Relayer. We are the first to formalize the BEV relay concept as an extension of the P2P transaction fee auction model. Contrary to the suggestions of the practitioner community, we find that a BEV relayer does not substantially reduce the P2P network overhead from competitive trading.
For our system model, we consider a blockchain system on top of a P2P network. We assume the existence of a trader V conducting at least one blockchain transaction TV (given a public/private key-pair) by, e.g., trading assets on AMM exchanges or interacting with a lending platform. The trader is free to specify its slippage tolerance, transaction fees, and choice of platform. We refer to the trader as a victim if other traders attack the trader (e.g., in a sandwich attack). We further assume the existence of a set of miners that may or may not engage in extracting blockchain extractable value. The miners can choose to order transactions according to internal policies or may follow the transaction fee distribution.
Our threat model captures a financially rational adversary A that is well-connected in the network layer to observe unconfirmed transactions in the memory pool. A holds at least one private key for a blockchain account from which it can issue an authenticated transaction TA. We also assume that A owns a sufficient balance of the native cryptocurrency (e.g., ETH on Ethereum) to perform actions required by TA, e.g., paying transaction fees or trading assets. If A is a mining entity, then A can unilaterally decide which and in which order transactions figure within its mined blocks. When A is a non-mining entity, A attempts to extract value by adjusting the transaction fees or resorting to BEV relayers (cf. Section VI-A in the paper).
Conclusion?
In this paper we shed light on the practices of obscure and predatory traders on blockchains. We provide empirical data for the state-of-the-art BEV, by notably studying past sandwich attacks and arbitrage on seven decentralized exchanges as well as liquidations on three lending platforms. To the best of our knowledge, we are the first to provide a generalized realtime replay trading algorithm. We alarmingly observe that the emerging BEV relayer endanger the blockchains’ security. We hope that our work provides insights into the current practices, and further helps to improve DeFi and blockchain security.