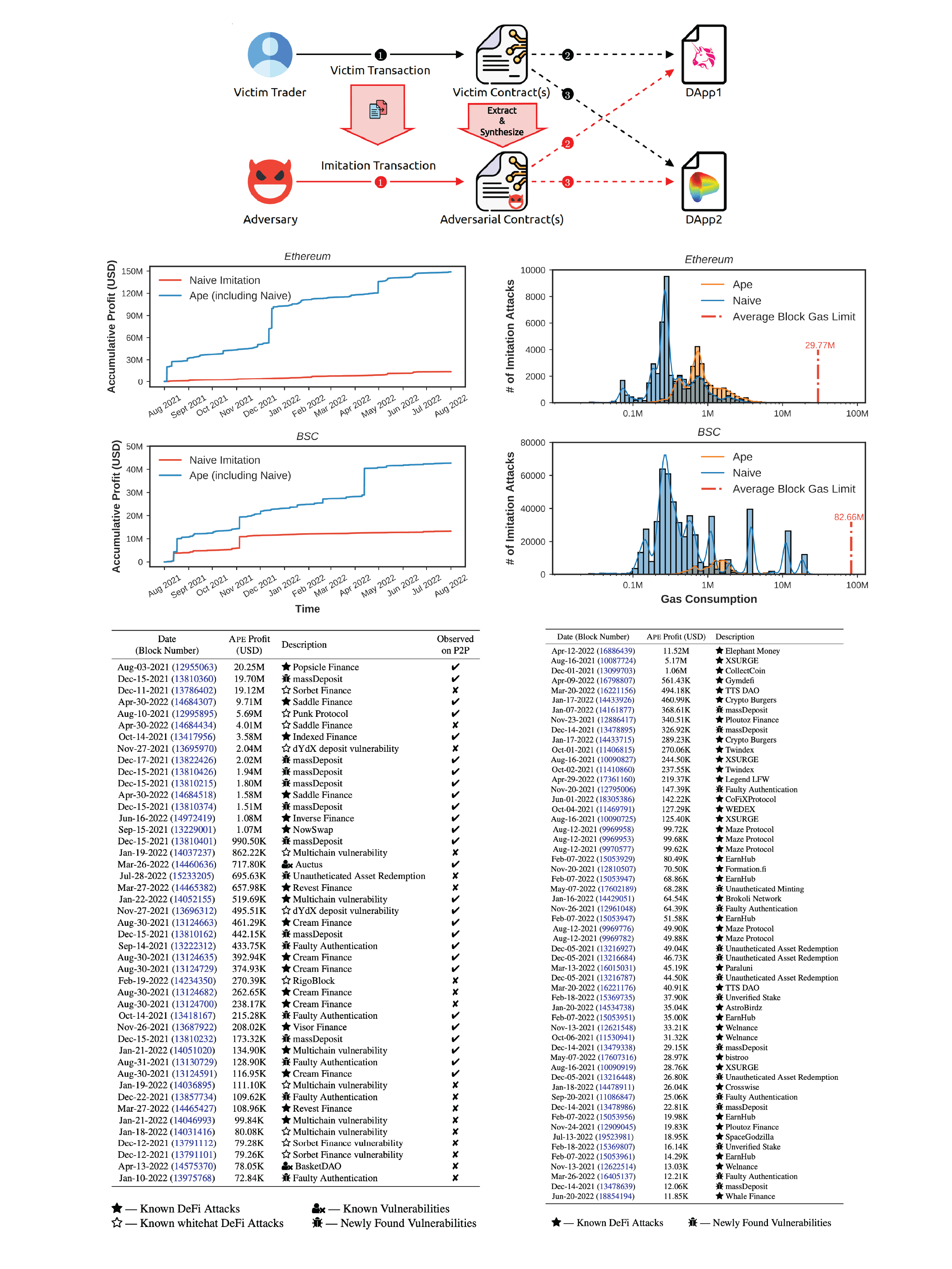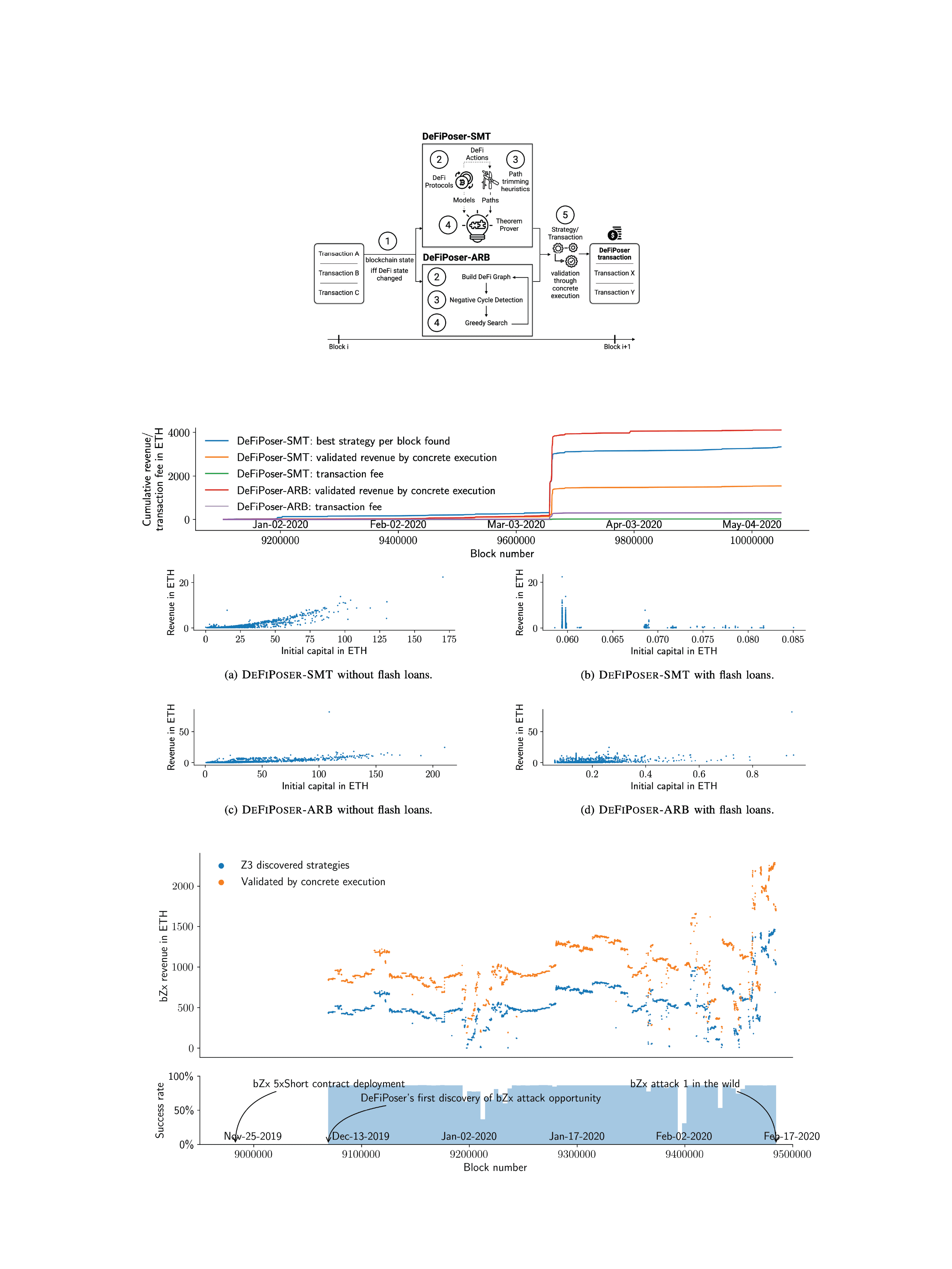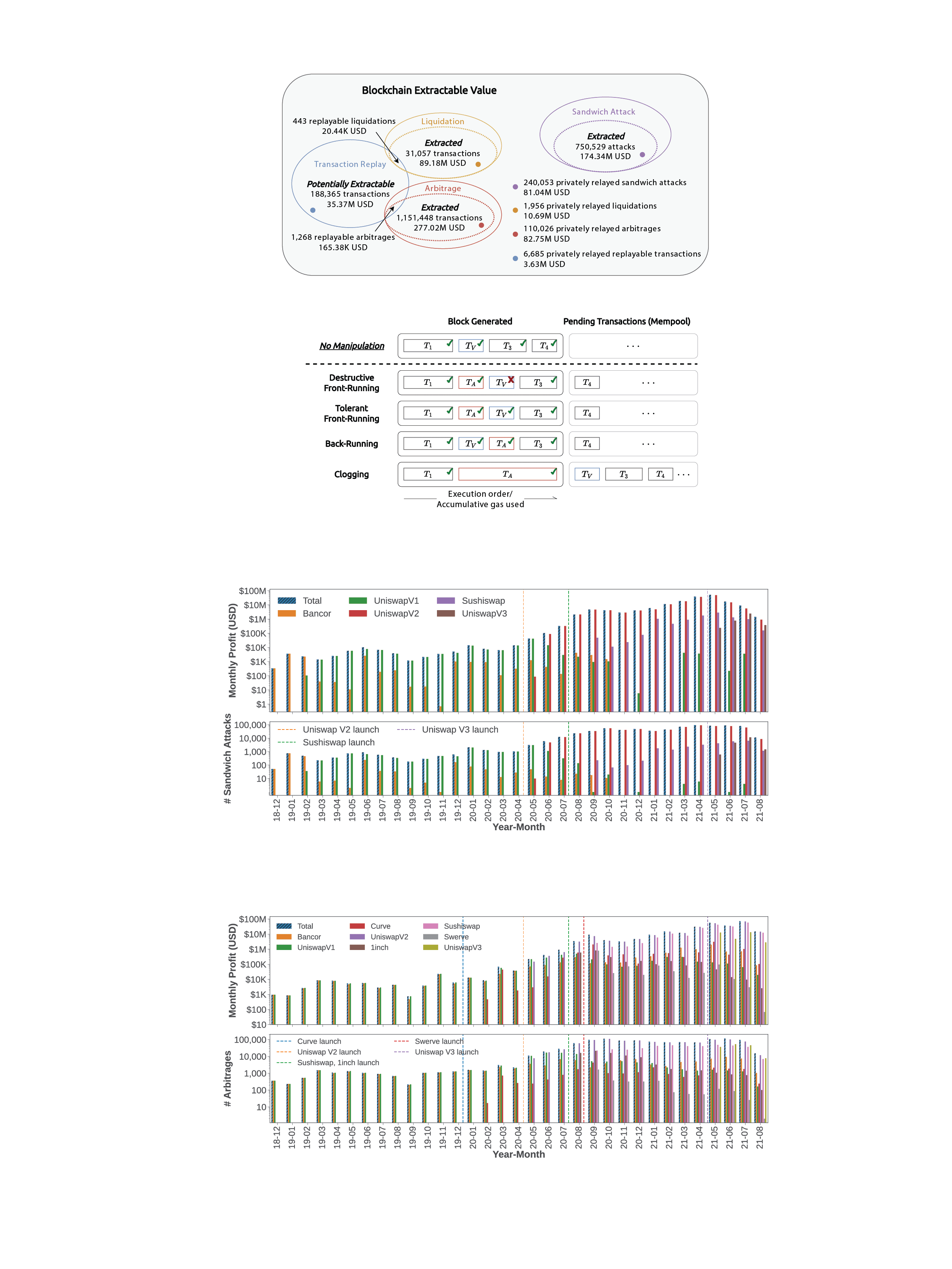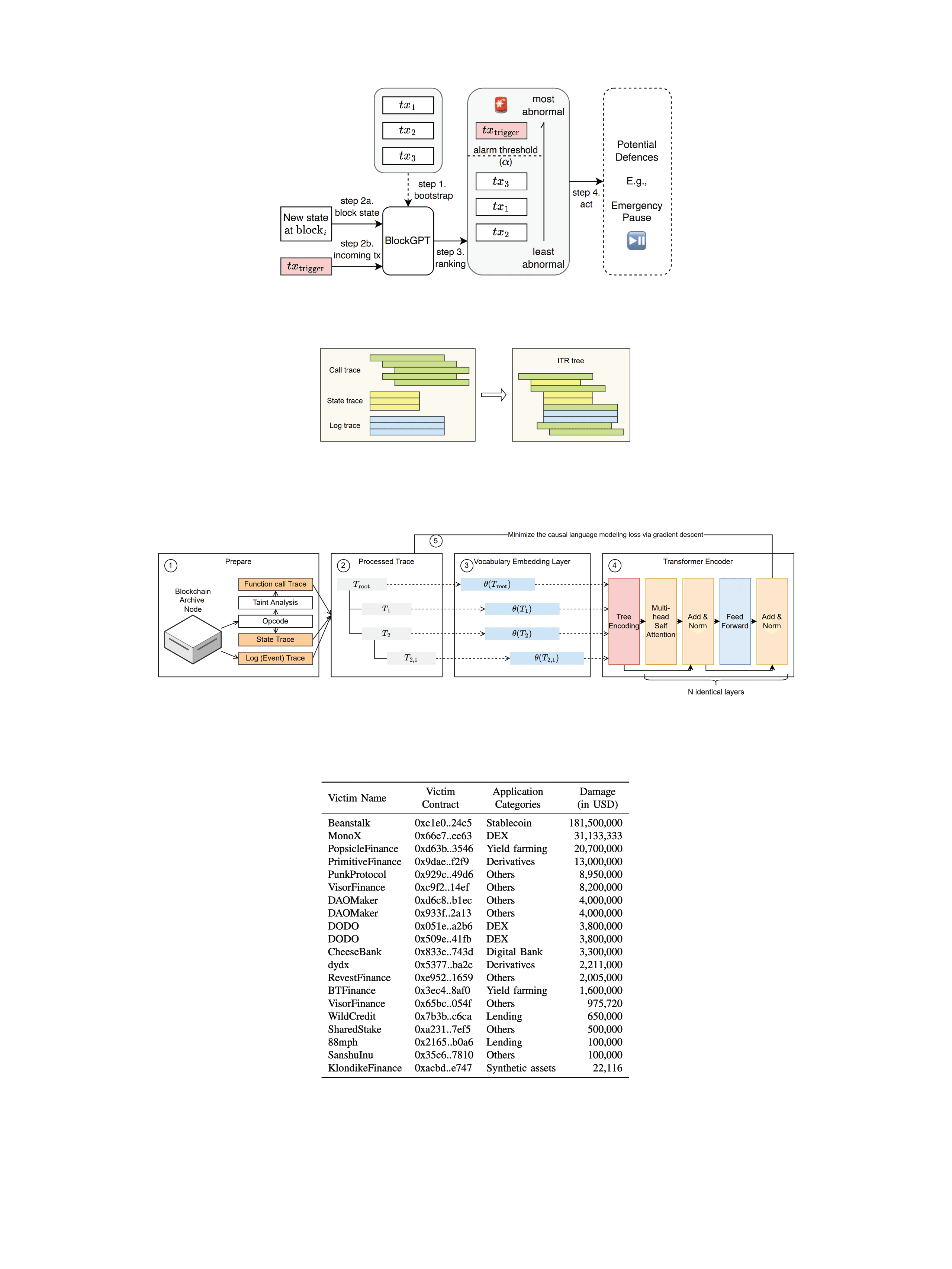
LLMs can learn how normal, and abnormal transactions look like
LLMs are wonderful at predicting the next character in a text. But they can also predict the next trace opcode of a blockchain transaction! Hence they can detect which next opcode is rather unlikely --- we use this insight to create an abnormality detection system.

Liyi Zhou